4 Ways to Make Your Data More Secure
von Jacob Davis | Aktualisiert: 07/15/2015 | Kommentare: 0
Your data is valuable, and sometimes that value is reduced if unauthorized users have access to it. For this reason, Campbell Scientific dataloggers have numerous methods of restricting access to your data. This article is an overview of four available methods for securing your data.

#1 - Security Codes
The most basic access control on the dataloggers is the Security Code. The Security Code is similar to a PIN (personal identification number) to unlock your cell phone. The Security Code feature has been available for more than 20 years.
A unique feature of Security Codes is that you may specify codes for three different levels of security. You could give one code to your field technician that only lets the technician view and collect data. For yourself, you could have the highest level code, which allows you to make setting changes, etc.
The Security Code settings do provide enough access restriction for many situations. However, a determined criminal can discover a PIN through a brute-force attack.
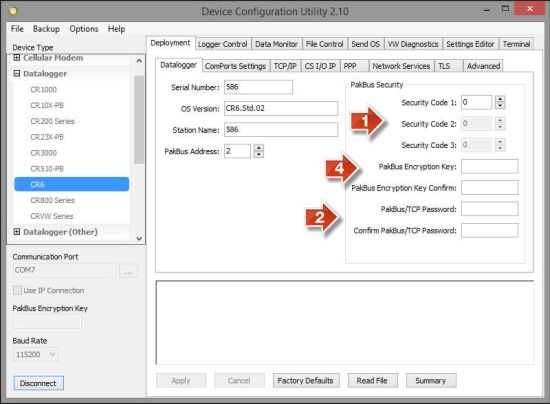
Location of three of the security settings in DevConfig.
#2 - PakBus/TCP Password
As IP connections have become very common with our dataloggers, Campbell Scientific has added PakBus/TCP Password as a means of authentication. You use the PakBus/TCP Password as a key with a proprietary authentication method similar to CRAM-MD5.
As the name of the setting implies, this setting only secures PakBus communication over TCP connections. It will not control access over a direct serial connection to your datalogger.
Although the PakBus/TCP authentication is practically impossible for a hacker to crack, the contents of the PakBus packets are not encrypted. A professional team of hackers could, in theory, listen to the IP traffic and try to guess which numbers are which measurements.
#3 - TLS
Another available form of security for IP connections is the industry standard TLS. TLS is the kind of security used when you log in to your bank’s website. Establishing a connection requires authentication, and the contents of the data packets are encrypted. The TLS connection won’t be cracked, unless you use “password” as your password.
The use of TLS is controlled by your datalogger program, not by settings. If you have used EmailSend() or FTPClient(), you may have used TLS without realizing it.
TLS is managed per individual IP connections. Due to the processing overhead, using your datalogger as a TLS server is impractical. However, when the datalogger connects to a TLS server as a client, performance is not overly affected.
#4 - PakBus Encryption Key

The PakBus Encryption Key is the evolution of the Security Code. It requires all PakBus communication to the datalogger to be authenticated and encrypted. The encryption used is AES-128, which is accepted as a very secure standard.
The PakBus Encryption Key secures both direct serial connections and IP connections. With it, you either have full access or no access.
Using Multiple Security Methods
It is possible for you to use these security methods simultaneously. For example, for ultimate security on PakBus connections over IP, you could enable the Security Code, PakBus/TCP Password, and PakBus Encryption Key. That is three layers of security! Just don’t forget your passwords. Not even our engineers could break through that security.
Tip: Take into consideration the physical security of the datalogger. It is possible for a knowledgeable person with physical access to the datalogger and a CR1000KD to acquire full access to the datalogger.
|
Recommended for You: Read the “How can data be made more secure on a CRBasic PakBus datalogger?” FAQ. |
Do you have a security story you’d like to share? Post it as a comment below.
Looking Ahead: If you use removable memory cards with your datalogger, you can look forward to a future article about the CRBasic Encryption() instruction.




 Jacob Davis is the Director of Client Services and Support at Campbell Scientific, Inc. He works with the worldwide technical support teams. His specialties include serial communications and advanced data logger programming. Jacob has a master’s degree in hydrology and worked with large irrigation projects before coming to Campbell Scientific, Inc.
Jacob Davis is the Director of Client Services and Support at Campbell Scientific, Inc. He works with the worldwide technical support teams. His specialties include serial communications and advanced data logger programming. Jacob has a master’s degree in hydrology and worked with large irrigation projects before coming to Campbell Scientific, Inc.
Kommentare
Please log in or register to comment.